Securing qconn
QNX Tool SuiteIntegrated Development Environment User's GuideDeveloperSetup
By default, the traffic sent to qconn is unencrypted, which leaves it vulnerable to interception. You can encrypt this traffic by tunnelling it through ssh, which ensures that the traffic is secure.
To implement this security feature:
The target has to have sshd installed and configured with either password authentication or public key authentication for the root user. You should therefore see files like the following on the target:
/etc/ssh/ssh_host_rsa_key
/etc/ssh/ssh_host_rsa_key.pub
/etc/ssh/sshd_configYou may see different files if you're using a different authentication protocol (e.g., DSA).
- The host has to have an SSH client.
- On the target, run sshd.
-
Start the qconn agent on the target, while specifying that it should accept connections only from
the local host:
qconn bind=127.0.0.1 -
On the host, establish an SSH tunnel by running ssh with the proper
options:
ssh qnxuser@target_host -N -L local_port:localhost:target_portwhere:-Ninstructs ssh to not run a shell.-L local_port:localhost:target_portspecifies the local (host machine) port used for tunnelling (e.g., 9000), followed by the keyword localhost (alternatively, you could use the address 127.0.0.1), then the target port where qconn is running (usually 8000).
Note:Depending on the SSH client program (e.g., PuTTY), you might have to manually specify the local and remote ports through UI fields instead of running the above command. -
When creating a target connection in the IDE, instead of specifying the target's IP address and port,
you must specify the local IP port used for SSH tunnelling, as shown below.
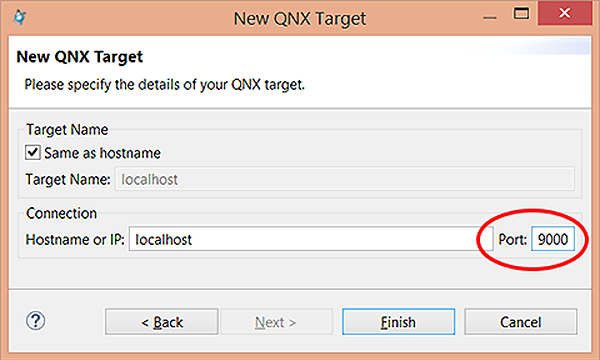 This setting makes the IDE connect to the target through the established SSH tunnel. The SSH service will forward all traffic from the local port to the target port.
This setting makes the IDE connect to the target through the established SSH tunnel. The SSH service will forward all traffic from the local port to the target port.
Page updated:
