By default, the traffic sent to qconn is unencrypted, which leaves it vulnerable to interception. You can encrypt this traffic by tunnelling it through ssh, which ensures that the traffic is secure.
To implement this security feature:
- The target has to have sshd installed and configured with either password authentication or public key authentication for the root user. You should therefore see files like the following on the target:
/etc/ssh/ssh_host_rsa_key
/etc/ssh/ssh_host_rsa_key.pub
/etc/ssh/sshd_configYou may see different files if you're using a different authentication protocol (e.g., DSA).
- The host has to have an SSH client.
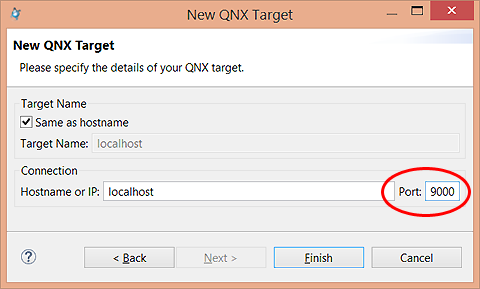
To configure a secure connection between the host and target: