The secure boot mechanism is based on the concept of a chain of trust. This kind of chain is anchored (rooted), and the root (for example: a factory-blown key hash) is inherently trusted. The root of trust requires a public key that is known to the firmware. From there, a private key is used to sign files such as the IFS image.
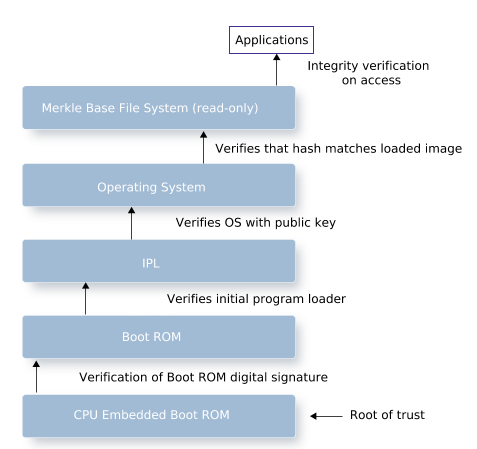
Systematic validation during boot-up starts at the root of trust and extends to boot ROMs, primary/secondary boot loaders, IPLs, and IFS images. Each subsequent piece of firmware and software in the boot process is cryptographically validated by its predecessor.
When a securely booted system is up and running, it is considered secure unless the root of trust has been compromised. If the contents of the secured IFS image change after boot-up, the board will not reboot.
Securing the image helps defend against low-level attacks. A trusted environment begins with a trusted platform. A secure (trusted) boot means that an IFS image will not boot on the board if the image has been compromised. A compromised image will not load.
Merkle filesystems provide integrity protection via a hash tree of all filesystem blocks which are verified on demand. The root hash of the tree is signed with a key pair providing assurance that the filesystem has not been tampered with. Accessing a part of the filesystem which fails the integrity check returns an error.
To learn more about how to install and build a QNX BSP, see:
- its supporting BSP User Guide
- the Building Embedded Systems guide
- the Release Notes for any additional board-specific instructions
For additional information on how to secure a specific board for boot-up, refer to the vendor's notes for the board.